Security Configuration
Contents
- 1 Role Based Access Controls (RBAC)
- 2 System Setup Security Checks
- 2.1 Change Your Passwords
- 2.2 Port Lock-down via IP Tables configuration
- 2.3 Changing the SSL Key for QuantaStor Web Management Interface
- 2.4 Custom SSL Certificates and TLS Security
- 2.5 Custom SSH Ciphers and Key Exchange Algorithms
- 2.6 Customizing Firewall Settings to Block Services
- 2.7 Enabling Duo Multi-Factor Authentication Documentation
- 2.8 Security Updates
- 2.9 IPSec
Role Based Access Controls (RBAC)
QuantaStor includes Role Based Access Control (RBAC) with Advanced User Security by masking user permissions and allowing administrators to grant permissions for users at the storage object level, to all objects in the user's associated cloud(s) or to the entire storage system.
User Management
Role Management
User Group Management
Resource Group / Tenant Management
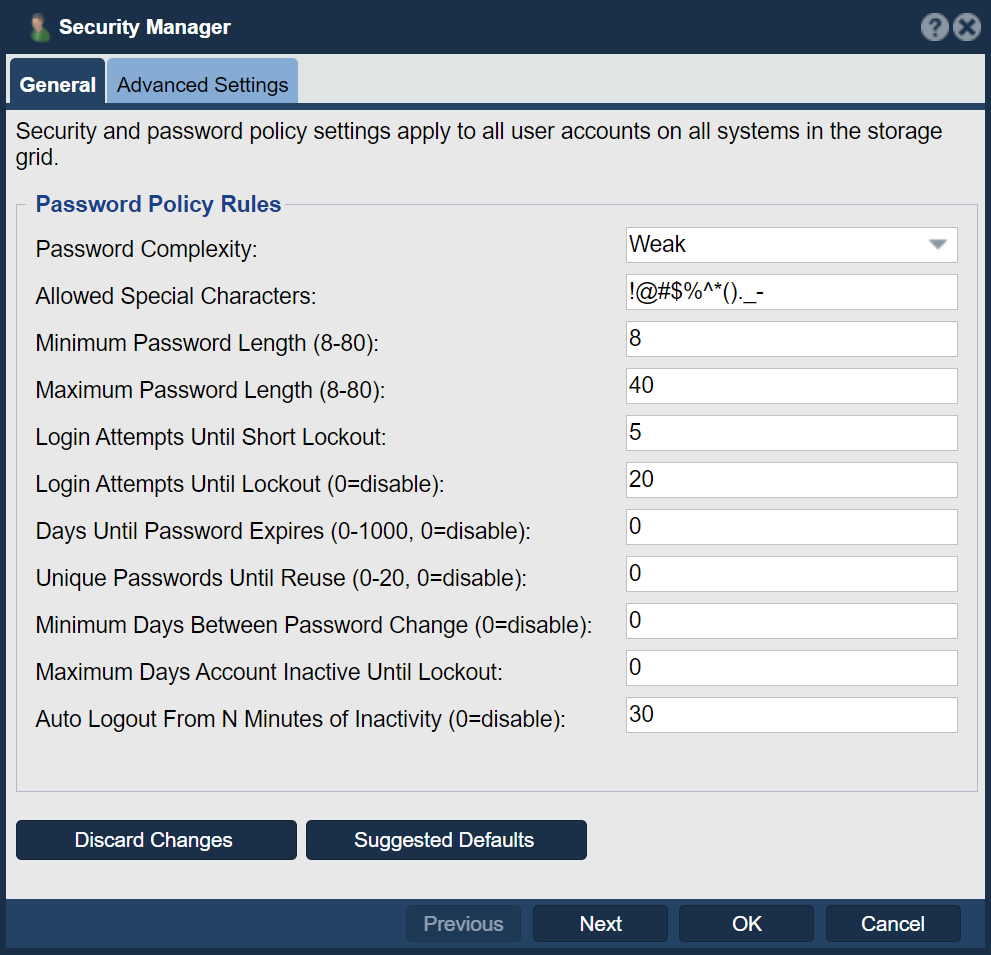
System Setup Security Checks
Change Your Passwords
One of the most important steps in the configuration of a new QuantaStor system is to just change the admin password for the system to something other than the default. You'll want to start by logging into the console using the 'qadmin' account and 'qadmin' password. Next type 'passwd' and change the password from 'qadmin' to something else. Next you'll want to login to the web management interface and change the 'admin' account password from 'password' to something else.
Port Lock-down via IP Tables configuration
QuantaStor comes with non-encrypted port 80 / http access to the system enabled. For more secure installations it is recommended that port 80 and non-essential services are blocked. To disable port 80 access run this command:
sudo qs-util disablehttp
To re-enable port 80 access use:
sudo qs-util enablehttp
Note that the web management interface will still be accessible via https on port 443 after you disable http access.
Changing the SSL Key for QuantaStor Web Management Interface
The SSL key provided with QuantaStor is a common self-signed SSL key that is pre-generated and included with all deployments. This is generally OK for most deployments on private networks but for increased security it is recommended to generate a new SSL keystore for the Apache Tomcat server used to serve the QuantaStor web management interface.
Keystore Password Selection
IMPORTANT NOTE You must set the password for the keystore to 'changeit' (without the quotes) as this is the default password that Tomcat uses to unlock the keystore. If you do not want to use the default password ('changeit') you can select a password of your choice but you will also need to manually edit the connector section of the /opt/osnexus/quantastor/tomcat/conf/server.xml file to add a line containing the keystore password (example: keystorePass="YOURPASSWORD"). Here's an example of what that will look like if you select the password "YOURPASSWORD".
<Connector port="8443" protocol="HTTP/1.1" SSLEnabled="true"
maxThreads="150" scheme="https" secure="true"
keystoreFile="/opt/osnexus/quantastor/tomcat/conf/keystore"
keystorePass="YOURPASSWORD"
clientAuth="false" sslProtocol="TLS" />
New Keystore Generation
To generate a new keystore you'll need to do the following steps.
- Login to QuantaStor via the console or via SSH then generate a keystore using the keytool utility. It will prompt you to enter a bunch of data including name, company, location, etc. This will produce a new .keystore file in the current directory. Remember to use the default Tomcat 'changeit' password for the keystore unless you plan to edit the /opt/osnexus/quantastor/tomcat/conf/server.xml file to add your custom keystore password.
keytool -genkey -alias tomcat -keyalg RSA -validity 365
- Next, backup the original keystore file and then overwrite the original with your newly generated keystore file:
cp /opt/osnexus/quantastor/tomcat/conf/keystore ./keystore.qs.conf cp .keystore /opt/osnexus/quantastor/tomcat/conf/keystore mv .keystore keystore.custom
- Finally, restart tomcat services so that the new key is loaded.
service tomcat restart
IMPORTANT NOTE If you are using Firefox as your browser, you must clear the browser history in order to clear the old cached key information. If you don't clear the history you'll see that the "Confirm Security Exception" button will be greyed out and you won't be able to login to your QuantaStor system via https. IE and Chrome do not have this issue.
That's the whole process. Here's an example of what we enter into these fields as OSNEXUS Engineering, you'll want to put your own company name and other details here:
keytool -genkey -alias qs-tomcat -keyalg RSA -validity 365 Enter keystore password: Re-enter new password: What is your first and last name? [Unknown]: OSNEXUS What is the name of your organizational unit? [Unknown]: OSNEXUS Engineering What is the name of your organization? [Unknown]: OSNEXUS, Inc. What is the name of your City or Locality? [Unknown]: Bellevue What is the name of your State or Province? [Unknown]: Washington What is the two-letter country code for this unit? [Unknown]: US Is CN=OSNEXUS, OU=OSNEXUS Engineering, O="OSNEXUS, Inc.", L=Bellevue, ST=Washington, C=US correct? [no]: yes
Custom SSL Certificates and TLS Security
- Information on how to Generate and Install Custom SSL Certificates and set Custom TLS security settings.
Custom SSH Ciphers and Key Exchange Algorithms
- Information on how to customize the ssh service to enforce strong Cipher and Key Exchange Algorithms for SSH communication.
Customizing Firewall Settings to Block Services
- Guide outlines how to block NFS, CIFS, iSCSI and other protocol access in order to further lock down an system.
Enabling Duo Multi-Factor Authentication Documentation
- Information on enabling multi-factor authentication using DUO.
Security Updates
- How to apply security patches and get detail on what patches apply to QuantaStor
IPSec
- IPsec can be used to encrypt traffic for NFS and other protocols